Internet provides a two-way flow of traffic that may be undesirable in many organizations where some information may concern exclusively within the organization or for Intranet. Intranet is aTCP/IP network that is modeled after the Internet that only works within the organization. In order to delineate information meant only for the benefit of the organization or its Intranet and the other open to all or meant for Internet, some sorts of security measures need to be employed to control two-way flow of traffic. The measure known, as firewall is simply used for this purpose.

A firewall is a combination of software and hardware components that controls the traffic that flows between a secure network (usually an office LAN) and an insecure network (usually the Internet). Using rules defined by the system administrator. The firewall sits at the gateway of a network or sits at a connection between the two networks. All traffic, from one network to the other, passes through the firewall. The firewall stops or allows traffic based on the security policy as defined in rules' table.
The secure trusted network is said to be 'inside' the firewall; the insecure untrusted network is said to be 'outside' the firewall.
The firewall has to be configured to allow some traffic through, otherwise nobody on the inside could access the Internet, nor send Internet e-mail, nor send any information or data from network outside the firewall to the network inside the firewall or vice versa. The fact that it allows some traffic through provides a channel that could potentially be exploited, and could certainly carry viruses.
However, principally, the philosophy behind firewall can be thought of as a pair of mechanisms such as:
- It exists to block traffic
- It exists to permit traffic.
In brief, the basic aim of firewall is to provide only one entrance and exit to the network. There are firewalls, which block the undesirable traffic, another allows traffic.
Network Architecture for Firewall
The most important aspect of a: firewall is that it is at the entry point of the networked system it protects. This means essentially that the firewall is the first program that receives and handles incoming network traffic, and it is the last to handle outgoing traffic.
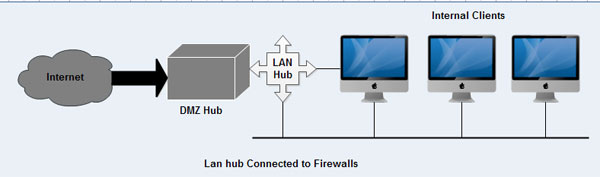
The logic is simple: a firewall must be positioned in a network to control all incoming and outgoing traffic. The internal network also needs to be structured and configured in such a way to implement security policy of firewall to protect specific services running on the systems. There are some sample examples of network structure to protect it from external threads using a firewall:
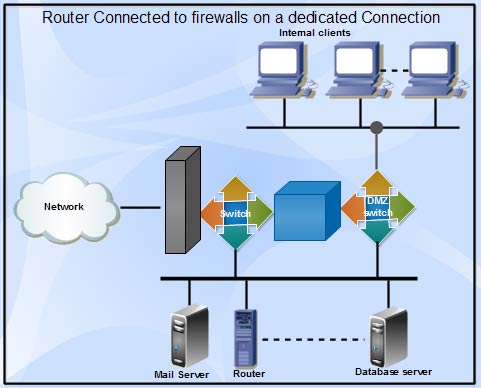
I. A router on dedicated connection to the Internet can be plugged into firewall system. This can also be provided with the help of a hub for full access servers outside firewall.
2. Router can be configured with some filtering rules. However, this router may be owned by ISP therefore, ISP may be asked to put all desired control.
3. On a dialup service like an ISDN line, a third network card is used to provide a filtered DMZ.
This gives full control over Internet services and still separates them from regular network.
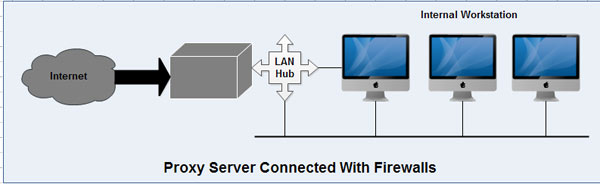
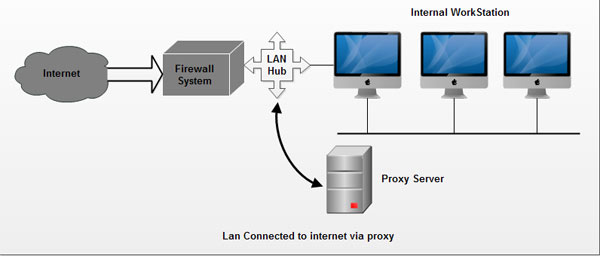
4. A proxy server can be used to monitor the traffic on the network and allowing the users to a limited number of services or some unwanted services may be blocked. This can be integrated with the firewall.
5. A proxy server on organization's LAN connected with the firewall should have rules to only allow the proxy server to connect to the Internet for the services it is providing. This way the users can get to the Internet only through the proxy.
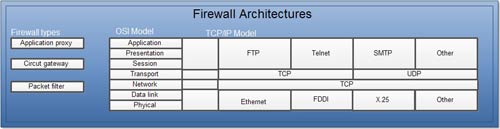
Relevance of OSI and TCP/IP layered Model with Firewall Architectures
All firewalls rely on the inspection of the information generated by protocols that function at various layers of the OSI (Open Systems Interconnection) model. Hence, the OSI layer has major role in designing the different types of firewall architectures
If a firewall architecture uses higher OSI layers to examine the information or within the packet, the firewall consumes more processor cycle (power), but architecture provides the greater level of protection.
A packet is a series of digital numbers basically, which conveys these things:
- The data, acknowledgment, request or command from the originating system
- The source and destination IP addresses
- The source and destination ports
- Information about the protocol (set of rules) by which the packet is to be handled
- Error checking information
- Usually, some sort of information about the type and status of the data being sent
- Often, a few other things too, which don't matter for our purposes here.
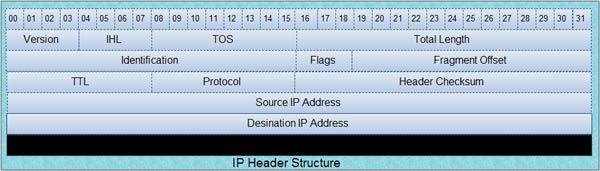
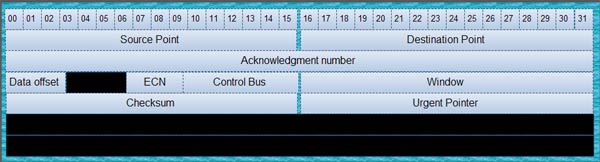
The important fields with TCP/IP Packets are:
The IP header structure is as follows:
The important fields with IP headers are:

The TCP header structure is as follows:
Types of Firewall Architectures
Conceptually, there are three types of firewalls:
- 1.Packet filter
- 2.Circuit filter
- 3.Application level filter
The level of protection that any firewall is able to provide in securing a private network when connected to the public Internet is directly related to the architecture(s) of the firewall. The generally available firewalls utilize following technologies for firewall architectures:
- Static packet filter
- Dynamic (state aware) packet filter
- Circuit level gateway
- Application level gateway (proxy)
- Stateful inspection
- Cutoff proxy
- Air gap.
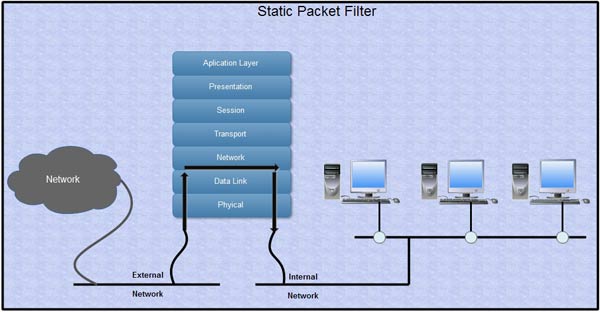
1. Static Packet Filter
All internet traffic travels in the form of packets. A packet is a quantity of data of limited size. When larger amount of continuous data is sent, it is broken up into numbered packets at the senders end for transmission and reassembled at the receiving end. The entire ·file downloads, Web page retrievals, emails - all these internet communications always occur in TCP /IP packets.
In packet filtering, only the protocol and the address information of each TCP/IP packet is examined. Its data contents and context (relation to other packets and to the intended application) are ignored. The firewall pays no attention to applications on the host or local network and "knows" nothing about the sources of incoming data.
Filtering consists of examining incoming or outgoing packets and allowing or disallowing their transmission or acceptance on the basis of a set of configurable rules, called policies.
Packet filtering policies may be based upon any of the following:
- Allowing or disallowing packets on the basis of the source IP address (sender)
- Allowing or disallowing packets on the basis of their destination port (service port)
- Allowing or disallowing packets according to protocol.
The packet filtering is usually made up of a series of checks based on the source and destination IP address and ports. A static packet filter operates at the network layer or OSI layer 3.
The decision to accept or deny a packet is based upon an examination of specific fields within the packet's TCP/IPheaders.
Before forwarding a packet, the firewall compares the IP header and TCP header against a user-defined table - rule base - which contains the rules that dictate whether the firewall should deny or permit packets to pass. The rules are scanned in sequential order until the packet filter finds a specific rule that matches the criteria specified in the packet-filtering rule. If the packet filter does not find a rule that matches the packet, then it imposes a default rule. The default rule explicitly defined in the firewall's table "typically" instructs the firewall to drop a packet that meets none of the other rules.
There are two approaches on the default rule used with the packet filter:
(a) Ease of use: Permits all traffic unless it is explicitly denied by prior rule. By default it is 'allow all' rule.
(b) Security first: Deny all traffic unless explicitly allowed by prior rule. By default it is 'deny all' rule.
Within the static packet filter rules database, the administrator can define rules that determine which packets are accepted and which packets are denied. The IP header information allows the administrator to write rules that can deny or permit packets to and from a specific IP address or range of IP addresses. The TCP header information allows the administrator to write service specific rules, i.e. allow or deny packets to or from ports related to specific services.
The administrator can write rules that allow certain services such as HTTP from any IP address to view the Web pages on the Web server. The administrator can also write rules that block certain IP address or entire ranges of addresses from using the HTTP service and viewing the web pages on the protected server. In the same respect, the administrator can write rules that allow certain services such as SMTP from a trusted IP address or range of IP addresses to access files on the protected mail server. The administrator could also write rules that block access for certain IP addresses or entire ranges of addresses to access the FTP server.
Problem with Static firewall
A packet filter only examines the information present in the IP header and TCP header; it does not know the difference between real and forged information. If an address is present and meets the packet filter rules along with the other rule criteria, the packet will be allowed to pass.
(i) IP Spoofing: Suppose, the administrator took the precaution to create a rule that instructed the packet filter to drop any incoming packets with unknown source addresses. This packet-filtering rule would make it difficult, but not impossible for a hacker to access at least some trusted servers with IP addresses. The hacker could simply substitute the actual source address on a malicious packet with the source address of a known trusted client. This common form of attack is called IP address spoofing. This form of attack is very effective against a packet filter.
(ii) Unaware of Packet Payload: The static packet filter does not examine packet payload, hence a hacker can hide malicious commands or data in unexamined headers. Further, since the static packet filter does not inspect the packet payload, the hacker has the opportunity to hide malicious commands or data within the packet's payload. This attack methodology is often referred to as a covert channel attack and is becoming more popular.
(iii) State unawareness: The static packet filter is not connection-state aware. Simply put, the administrator must configure rules for both sides of the ~conversation to a protected server. To allow access to a protected Web server the administrations create a rule, which allows both the inbound request from the remote client as well as the outbound response from the protected Web server. Of further consideration is that many services such as ITP and e-mail servers in operation today require the use of dynamically allocated ports for responses, so an administrator of a static packet filtering-based firewall has little choice but to open up an entire range of ports with static packet filtering rules.
Advantages
- Low impact on network performance
- Low cost.
Disadvantages
- Operates only at network layer therefore it only examines IP and TCP headers
- Unaware of packet payload-offers low level of security.
- Lacks state awareness-may require numerous ports be left open to facilitate services that use dynamically allocated ports.
- Susceptible to IP spoofing
- Difficult to create rules (order of precedence).
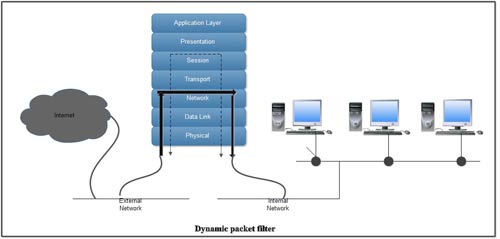
2. Dynamic (State Aware) Packet filter
A dynamic packet filter firewall is a fourth-generation firewall technology. A dynamic packet filter can monitor the state of active connections and use the information obtained to determine which network packets to allow through the firewall. By recording session information such as IP address and port numbers, a dynamic packet filter combines the best of application level gateways with simple packet filters to make it secure and fast.
It shares many of the inherent limitations of the static packet filter with one important difference: state awareness. This is particularly relevant to UDP packets.
The typical dynamic packet filter, like the static packet filter, operates at the network layer or OSI layer 3. An advanced dynamic packet filter may operate up into the transport layer-OSI layer 4 to collect additional state information.
Most often, the decision to accept or reject a packet is based upon examination of the packet's IP and protocol headers.
In simplest terms, the typical dynamic packet filter is "aware" of the difference between a new and an established connection. Once a connection is established, it is entered into a table that typically resides in RAM. Subsequent packets are compared to this table in RAM, most often, by software running at the operating system (OS) kernel level. When the packet is found to be an existing connection, it is allowed to pass without any further inspection. By avoiding having to parse the packet filter rule base for each and every packet that enters the firewall and by performing this already established connection table test at the kernel level in RAM, the dynamic packet filter enables a measurable performance increase over a static packet filter.
Advantages
- Low cost
- State awareness provides measurable .performance benefit, scalability and extensibility.
Disadvantages
- Operates only at network layer therefore, it only examines IP and TCP headers.
- Unaware of packet payload-offers low level of security
- Susceptible to IP spoofing
- Difficult to create rules (order of precedence)
- Can introduce additional risk if connections
- Can be established without following the RFC-recommended 3 way-handshake.
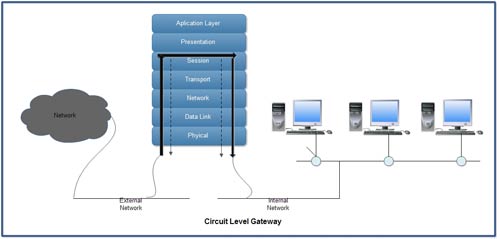
3. Circuit level Gateway
Level Gateway
The circuit level gateway operates at the session layer-OSI layer 5. In many respects, a circuit level gateway is simply an extension of a packet filter in that it typically performs basic packet filter operations and then adds verification of proper handshaking of TCP and the legitimacy of the session information used in establishing the connection. Hence, the circuit level gateway has more data to act upon than a standard static or dynamic packet filter
Before allowing data to be exchange, the firewall first validates connection. Whether a connection is valid may be based upon:
- Source IP address and/or port
- Destination IP address and/or port
- Application or protocol
- User and password
- Handshaking and sequence numbers.
Most often, the decision to accept or reject a packet is based upon examining the packet's IP header and TCP header.
Similar to a packet filter, before forwarding the packet, a circuit level gateway compares the IP header and TCP header against a user-defined table containing the rules that dictate whether the firewall should deny or permit packets to pass. The circuit level gateway then determines that a requested session is legitimate only if the SYN flags, ACK flags and sequence numbers involved in the TCP handshaking. between the trusted client and the untrusted host are logical.
If the session is valid, the packet filter rules are scanned until it finds one that agrees with the information in a packet's full association. If the packet filter does not find a rule that applies to the packet, then it imposes a default rule. The default rule explicitly defined in the firewall's table "typically" instructs the firewall to drop a packet that meets none of the other rules.
The circuit level gateway is literally a step up from a packet filter in the level of security it provides. Further, like a packet filter operating at a low level in the OSI model; it has little impact on network performance. However, once a circuit level gateway establishes a connection, any application can run across that connection because 'l. circuit level gateway filters packets only at the session and network layers of the OSI model. In other words, a circuit level gateway cannot examine the data content of the packets it relays between a trusted network and an untrusted network. The potential exists to slip harmful packets through a circuit level gateway to a server behind the firewall.
Benefits
- Low to moderate impact on network performance
- Breaks direct connection to server behind firewall
- Higher level of security than a static or dynamic (state aware) packet filter
- Provides services for a wide range of protocols.
Drawbacks
- Shares many of the same negative issues associated with packet filters
- Allows any data to simply pass through the connection
- Only provides for a low to moderate level of security.
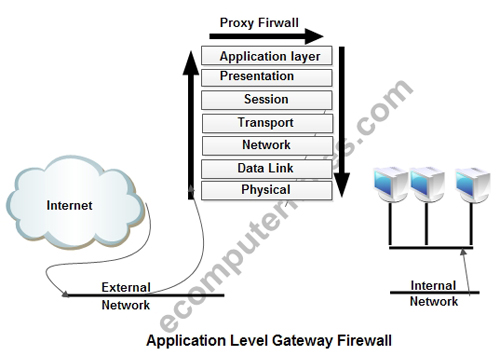
4. Application level Gateway
A firewall that filters information at the application level blocks all IP traffic between the private network and the Internet. No IP packets from the clients or servers of the private network are allowed to enter or leave the Internet.
Instead, this type of firewall operates according to what is referred to as the proxy principle. This means that internal clients set up connections to the firewall and communicate with a proxy server. If the firewall decides that the internal client should be allowed to communicate, it sets up a connection with the external server and performs the operation on behalf of the client. This method solves many of the security problems associated with IP.
Each proxy server uses a particular application protocol, such as http-proxy or ftp-proxy. The proxy firewall uses a combination of different proxy servers which allows many different applications to be handled.
In addition to providing the best security, the proxy firewall can be used to fetch and store information from the Internet in a cache memory. The proxy firewall can achieve short response and download times because it "understands" the application programs and can see which URLs are most in demand.
Like a circuit level gateway, an application level gateway intercepts incoming and outgoing packets, acts as a proxy for applications, providing information exchange across the gateway. It also functions as a proxy server, preventing any direct connection between a trusted server or client and an untrusted host. The proxies that an application level gateway runs often differ in two important ways from the circuit level gateway:
- The proxies are application specific
- The proxies examine the entire packet and can filter packets at the application layer of the OSI model.
Unlike the circuit gateway, the application level gateway accepts only packets generated by services. They are designed to copy, forward and filter. For example, only an HTTP proxy can copy, forward and filter HTTP traffic. If a network relies only on an application level gateway, incoming and outgoing packets cannot access services for which there is no proxy. For example, if an application level gateway ran ITP and HTTP proxies, only packets generated by these services could pass through the firewall. All other services would be blocked.
The application level gateway runs proxies that examine and filter individual packets, rather than simply copying them and recklessly forwarding them across the gateway. Application specific proxies check each packet that passes through the gateway, verifying the contents of the packet up through the application layer (layer 7) of the OSI model. These proxies can filter on particular information or specific individual commands in the application protocols the proxies are designed to copy, forward and
As an example, an application level proxy is able to block FTP put commands while permitting FTP get commands.
Current technology application level gateways are often referred to as strong application proxies. A strong application proxy extends the level of security afforded by the application level gateway. Instead of copying the entire datagram on behalf of the user, a strong application proxy actually creates a brand /I new empty datagram inside the firewall. Only those commands and data found acceptable to the strong application proxy are copied from the original datagram outside the firewall to the new datagram inside the firewall. Then, and only then, is this new datagram forwarded to the protected server behind the firewall. By employing this methodology the strong application proxy can mitigate the risk of an entire class of covert channel attacks.
An application level gateway fitters information at a higher OSI layer than the common static or
dynamic packet filter, and most automatically create any necessary packet filtering rules, usually making them easier to configure then traditional packet filters.
Benefits
- Better logging handling of traffic (because all data between the client and the server is routed through the application proxy it is able to both control the session and provide detailed logging; This ability to log and control all incoming and outgoing traffic is one of the main advantages of application level gateway
- State aware of services (FTP, XII, etc.)
- Packet air gap like architecture, i.e. breaks direct connection to server behind firewall eliminating
- the risk of an entire class of covert channel attacks
- Strong application proxy that inspects protocol header lengths can eliminate an entire class of
- buffer overrun attacks
- Highest level of security.
Weaknesses
- A poor implementation that relies on the underlying as Inetd daemon will suffer from a severe limitation to the number of allowed connections in today's demanding high simultaneous session environment.
- Complex setup of application firewall needs more and detailed attentions to the applications that use the gateway.
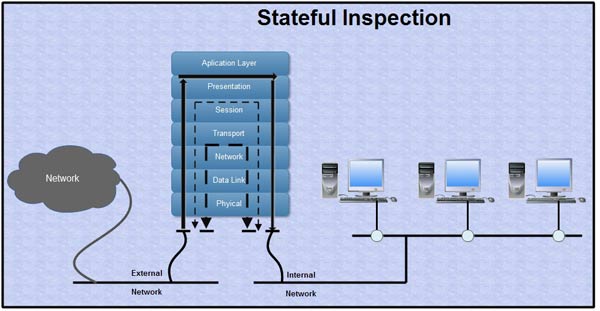
5. Stateful Inspection
Stateful inspection combines the many aspects of dynamic packet filtering, circuit level and application level gateways.
As indicated, stateful inspection can also function as a circuit level gateway, determining whether the packets in a session are appropriate. For example, stateful inspection can verify that inbound SYN and ACK flags and sequence numbers are logical: However, in most implementations the stateful inspection-based firewall operates only as a dynamic packet filter and, dangerously, allows new connections to be established with a single SYN packet.
A unique limitation of one popular stateful inspection implementation is that it does not provide the ability to inspect sequence numbers on outbound packets from users behind the firewall. This leads to a flaw whereby internal users can easily spoof IP address of other internal users to open holes through the associated firewall for inbound connections.
Finally, stateful inspection can mimic an application level gateway. Stateful inspection can evaluate the contents of each packet up through the application layer and ensure that these contents match the rules in the administrator's network security policy.
Benefits
- Offers the ability to inspect all seven layers of the OSI model and is user configurable to customize specific filter constructs
- Does not break the client server model
- Provides an integral dynamic (stateful) packet filter
- Fast when operated as dynamic packet filter, however many SMP-compliant dynamic packet filters are actually faster.
Weaknesses
- The single-threaded process of the stateful inspection engine has a dramatic impact on performance, so many users operate the stateful inspection based firewall as nothing more than a dynamic packet filter
- Many believe the failure to break the client server model creates an unacceptable security risk as the hacker has a direct connection to the protected server
- A poor implementation that relies on the underlying OS Inetd demon will suffer from a severe limitation to the number of allowed connections in today's demanding high simultaneous session environment
Low level of security. No stateful inspection based firewall has achieved higher than a Common Criteria EAL 2. Per the Common Criteria EAL 2 certification documents, EAL 2 products are not intended for use in protecting private networks when connecting to the public Internet.
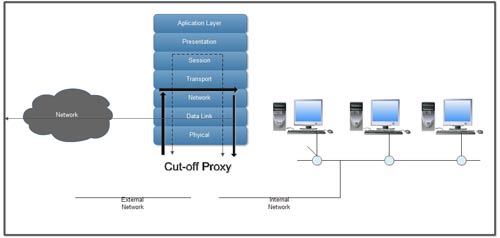
6. Cutoff Proxy
The cutoff proxy is a hybrid combination of a dynamic (stateful) packet filter and a circuit level proxy. In simplest terms, the cutoff proxy first acts as a circuit level proxy in verifying the RFC-recommended three-way handshake and any required authenticating actions, then switches over to a dynamic packet filtering mode of operation. Hence, it initially works at the session layer-OSI layer 5; then switches to a dynamic packet filter working at the network layer OSI Layer 3. After the connection, authentication process is completed.
The cutoff proxy verifies the RFC-recommended three-way handshake" provides for limited application-based authentication and then switches to a dynamic packet filter mode of operation.
The cutoff proxy is not a traditional circuit level proxy that breaks the client/server model for the duration of the connection. There is a direct connection established between the remote client and the protected server behind the firewall. This is not to say that a cutoff proxy does not provide a useful balance between security and performance. The cutoff proxy offers a level of security equivalent to a traditional circuit level gateway with the added benefit of the performance of a dynamic packet filter.
If the security policy requires authentication of basic services, examination of the three-way handshake and does not require breaking of the client/server model, the cutoff proxy is a good fit. However, administrators must be fully aware and understand that a cutoff proxy clearly is not equivalent to a circuit level proxy as the client/server model is not broken for the duration of the connection.
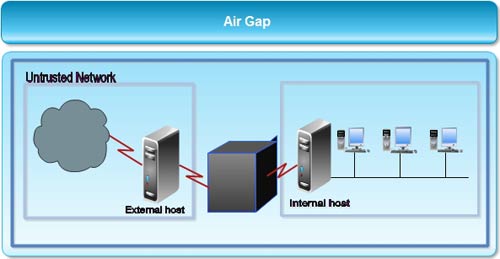
7. Air Gap
The latest entry into the array of available firewall architectures is the air gap. This is an extreme kind of firewall where there is no direct or automated connection between two devices.
Air gap technology provides a physical gap between trusted and untrusted networks, creating an isolated path for moving files between an external server and a company's internal network and systems.
In air gap technology, the external client connection "causes the connection data to be written to an SCSI e-Disk. The internal connection then reads this data from the SCSI e-Disk. By breaking the direct connection between the client to the server and independently writing to and reading from the SCSI e-Disk, a higher level of security is provided and a resultant "air gap."
The basic operation of air gap technology closely resembles that of the application level gateway.
Advantage of Air-gap
- Inside is insulated from outside
- Packets are not "automatically" passed through
- Only explicitly launched services work
- No unexpected traffic via other sockets.
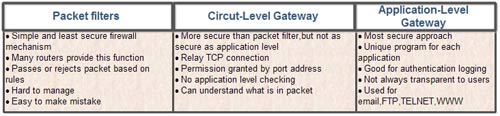
Difference between Packet Filters, Circuit-Level Gateway and Application-Level Gateway

Great breakdown of firewall architectures! Understanding these structures is crucial for cybersecurity. Businesses seeking top-tier Firewall Solutions Dubai can benefit from these insights!
ReplyDelete