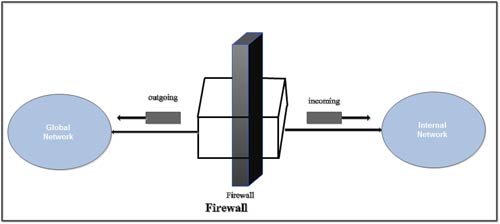
A firewall is a device installed between the internet network of an organization and the rest of Internet. When a computer is connected to Internet, it can create many problems for corporate companies. Most companies put a large amount of confidential information online. Such an information should not be disclosed to the unauthorized persons. Second problem is that the virus, worms and other digital pests can breach the security and can destroy the valuable data.
1. Incoming packets from network 124.56.0.2 are block (* means any).
2. Incoming packets destined for any internal TELNET server (port 23) are blocked.
3. Incoming packets for internal host 156.255.7.8.8 are blocked.
4. Outgoing packets destined for an HTTP server (port 80) are blocked i.e. employees of organization are not allowed to browse the internet and cannot send any HTTP request.
The main purpose of a firewall is to separate a secure area from a less secure area and to control communications between the two. Firewall also controlling inbound and outbound communications on anything from a single machine to an entire network.
On the Other Hand Software firewalls, also sometimes called personal firewalls, are designed to run on a single computer. These are most commonly used on home or small office computers that have broadband access, which tend to be left on all the time.
A software firewall prevents unwanted access to the computer over a network connection by identifying and preventing communication over risky ports. Computers communicate over many different recognized ports, and the firewall will tend to permit these without prompting or alerting the user.
A firewall can serve the following functions:
1- Limit Internet access to e-mail only, so that no other types of information can pass between the intranet and the Internet
2- Control who can telnet into your intranet (a method of logging in remotely
3- Limit what other kinds of traffic can pass between your intranet and the
Internet .
A firewall can be simple or complex, depending on how specifically you want to control your Internet traffic. A simple firewall might require only that you configure the software in the router that connects your intranet to your ISP. A more complex firewall might be a computer running UNIX and specialized software.
Firewall systems fall into two categories
• network-level
• application-level.
Network-Level Firewalls
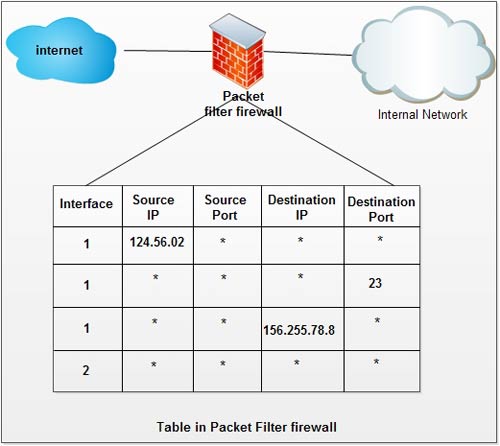
It can be used as packet filter. These firewalls examine only the headers of each packet of information passing to or from the Internet. The firewall accepts or rejects packets based on the packet’s sender, receiver, and port. For example, the firewall might allow e-mail and Web packets to and from any computer on the intranet, but allow telnet (remote login) packets to and from only selected computers.
Packet filter firewall maintains a filtering table that decides which packets are to be forwarded or discarded. A packet filter firewall filters at the network or transport layer.
As shown in fig. the packets are filtered according to following specifications :
1. Incoming packets from network 124.56.0.2 are block (* means any).
2. Incoming packets destined for any internal TELNET server (port 23) are blocked.
3. Incoming packets for internal host 156.255.7.8.8 are blocked.
4. Outgoing packets destined for an HTTP server (port 80) are blocked i.e. employees of organization are not allowed to browse the internet and cannot send any HTTP request.
Application-Level Firewalls
These firewalls handle packets for each Internet service separately, usually by running a program called a proxy server,which accepts e-mail, Web, chat, newsgroup, and other packets from computers on the intranet, strips off the information that identifies the source of the packet, and passes it along to the Internet.
When the replies return, the proxy server passes the replies back to the computer that sent the original message. A proxy server can also log all the packets that pass by, so that you have a record of who has access to your intranet from the Internet, and vice versa.
Great blog post! A well-configured firewall is crucial for securing networks. For businesses in need of robust protection, exploring Firewall Solutions Dubai can provide the advanced security you need.
ReplyDelete